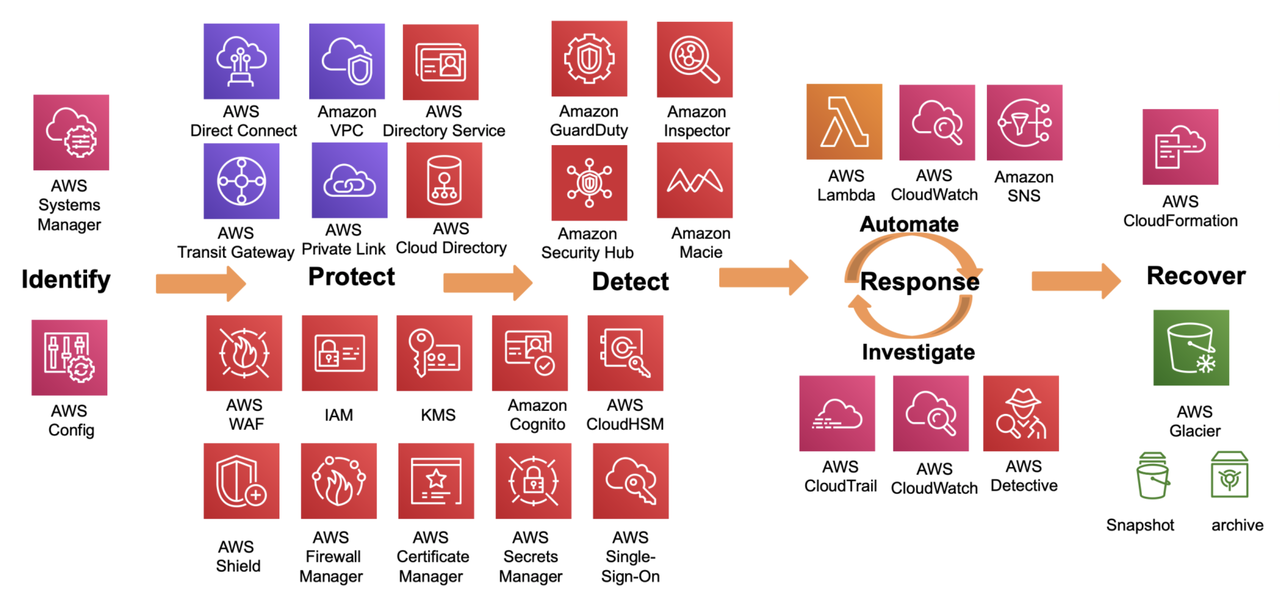
AWS Security Fundamentals - Building a Secure Cloud Environment
Security is one of the most critical aspects of working with cloud infrastructure, especially with a platform as comprehensive as AWS. Ensuring that your cloud environment is secure requires an understanding of AWS’s security tools and services, as well as adherence to best practices that align with your organization’s security and compliance goals. This blog post provides an in-depth look into AWS Security Fundamentals, focusing on tools like AWS Config, AWS CloudTrail, and key design principles that enhance security. We will break down each concept through the lens of a DevOps engineer and programmer to highlight practical applications and strategies.
Key AWS Security Principles and Best Practices
Implement a Strong Identity Foundation
The first key security principle is implementing a strong identity foundation. AWS emphasizes the principle of least privilege, which means granting only the permissions required for each user or process to perform their tasks. Implementing AWS Identity and Access Management (IAM) enables DevOps teams to control access to AWS resources effectively.
- AWS IAM provides tools for managing and creating access controls, such as users, groups, roles, and policies. A practical example is configuring a role-based access control system for a CI/CD pipeline, ensuring only the necessary permissions are granted to run builds or deployments.
- To further strengthen identity management, organizations can enforce Multi-Factor Authentication (MFA) and consider Single Sign-On (SSO) integrations for seamless and secure user access. These steps ensure that sensitive operations require not just a password, but an additional form of authentication, reducing the risk of unauthorized access.
AWS Identity and Access Management
Enable Traceability
AWS strongly recommends enabling traceability across your cloud resources. This means continuously monitoring changes and activities within the environment and maintaining comprehensive logging for all operations.
- AWS CloudTrail is a critical service that logs every API call made within your AWS account, offering insight into who accessed which resources and what actions they took. This helps in audit trails and forensic investigations after a security incident.
- To complement CloudTrail, AWS Config continuously monitors and records your AWS resource configurations. AWS Config provides a historical view of resource configurations, making it easier to audit the state of resources and ensure compliance with internal security policies.
Apply Security at All Layers
Rather than relying solely on protecting the perimeter, AWS encourages applying security at all layers within the cloud infrastructure. This multi-layered approach, also known as defense in depth, includes security controls at each level of the system.
- Examples include configuring security groups and network access control lists (NACLs) to define inbound and outbound traffic rules for instances and subnets. Applying these controls ensures that only allowed traffic can reach critical resources.
- Additional layers of security can be implemented using AWS Web Application Firewall (WAF) to protect against common exploits like SQL injection or cross-site scripting. This approach helps prevent attacks from reaching sensitive applications.
Automation and Data Protection
Automate Security Best Practices
One of the greatest strengths of AWS is the ability to automate security best practices. Automation not only improves the reliability of security processes but also scales with your infrastructure as it grows.
- Implement infrastructure as code (IaC) using tools like AWS CloudFormation or Terraform to enforce security controls consistently across environments. By defining security groups, IAM roles, and resource configurations in code, you ensure a standardized approach that reduces the risk of human error.
- Automated compliance checks using AWS Config Rules allow real-time enforcement of security policies. For example, you could create a rule that ensures all S3 buckets have encryption enabled, automatically notifying or remediating any violations.
Protect Data in Transit and at Rest
To maintain confidentiality and integrity, AWS provides tools to protect data in transit and at rest. This includes the use of encryption technologies and secure transmission protocols.
- Use AWS Key Management Service (KMS) to manage encryption keys for data stored in services like Amazon S3, RDS, or EBS. KMS allows customers to control the creation, rotation, and permissions of encryption keys to protect sensitive data.
- For data in transit, enforcing TLS/SSL ensures secure communication channels between clients and servers. Implementing VPC Peering and PrivateLink can also help to restrict data movement within private networks, reducing exposure.
Incident Response and Preparation
Prepare for Security Events
The final key security principle is to prepare for security events. Incident response is a critical component of any security plan, and being prepared involves both technical and procedural readiness.
- Establish an incident management plan that aligns with your organization’s compliance and business continuity requirements. AWS offers tools like AWS CloudWatch for monitoring, which can alert security teams to suspicious activities in real time.
- Run regular incident response simulations to test the effectiveness of your plan. Use tools like AWS Systems Manager Automation to create playbooks that can automatically respond to detected incidents, such as isolating a compromised instance or resetting IAM credentials.
DDoS Mitigation
Another aspect of preparation involves DDoS mitigation. AWS provides built-in tools, such as AWS Shield and AWS WAF, to help mitigate Distributed Denial of Service attacks.
- AWS Shield Standard automatically provides protection to all AWS customers, while AWS Shield Advanced offers more robust DDoS detection and mitigation tailored for business-critical workloads.
- Combining AWS WAF with CloudFront helps in adding another security layer to protect against web-based threats. This layered approach to DDoS protection ensures both infrastructure-level resilience and application-level security.
AWS Security Fundamentals emphasize a structured approach to building secure and resilient cloud environments. By focusing on principles such as implementing strong identity foundations, enabling traceability, automating security best practices, and preparing for security events, organizations can build a robust defense-in-depth strategy. AWS offers a suite of tools—like IAM, CloudTrail, KMS, and AWS Shield—to help fulfill these principles effectively.
For DevOps engineers and system administrators, understanding AWS security fundamentals is not just about compliance; it’s about empowering teams to build reliable, secure, and scalable infrastructure that meets the demands of today’s digital landscape. Start by mapping your security responsibilities and leveraging AWS tools to ensure a fortified cloud environment.
Looking to deepen your understanding of AWS security practices? Explore our detailed guides on AWS Security Hub and AWS Well-Architected Framework. These resources can help you elevate your cloud infrastructure security to the next level.