Protecting Your AWS Instances with Security Groups
Securing cloud infrastructure is a paramount concern for DevOps engineers and developers working on AWS. Security Groups play a crucial role in enhancing the security of your AWS instances by controlling inbound and outbound traffic. In this blog post, we will delve into the details of AWS Security Groups, understanding their importance in protecting your instances, and discussing their use compared to other mechanisms like Network Access Control Lists (NACLs). Throughout, we’ll provide a detailed perspective from the point of view of a DevOps engineer to offer deep technical insights.
Understanding Security Groups
What Are Security Groups?
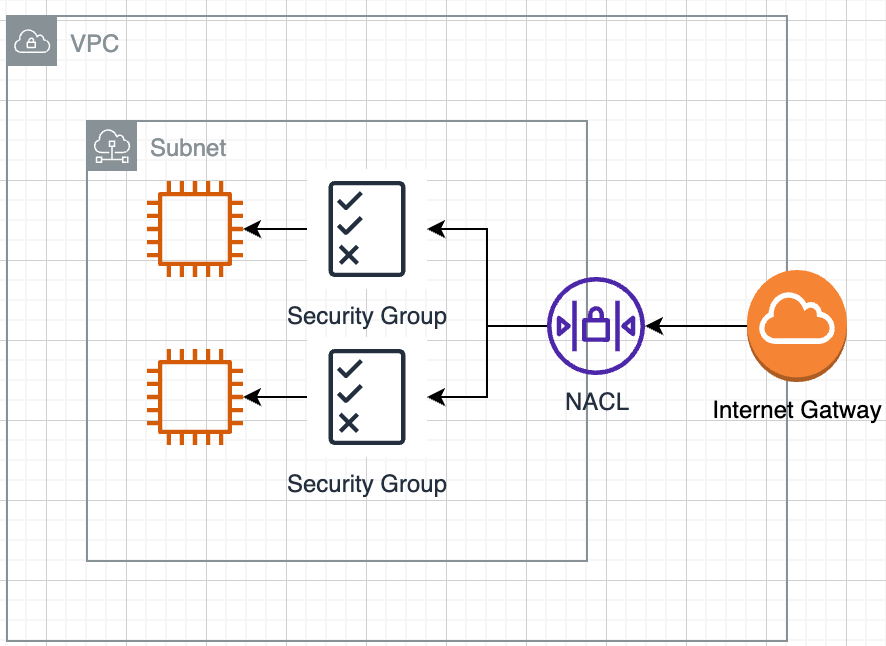
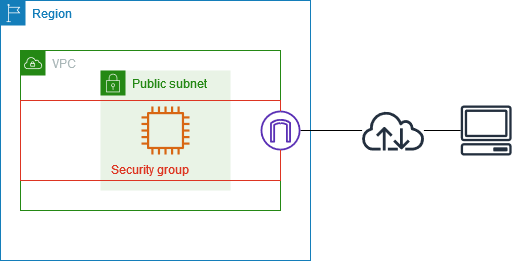
Security Groups are a fundamental part of Amazon Virtual Private Cloud (VPC) security settings. They act as virtual firewalls that control the traffic to and from your AWS instances. Security Groups can be configured with rules to allow or deny traffic based on specified criteria, providing a robust mechanism for managing network security.
Each Security Group operates at the instance level. This means it controls the traffic for each specific instance associated with it. Unlike Network Access Control Lists (NACLs), which control traffic at the subnet level, Security Groups provide a more granular layer of security.
AWS allows you to create rules that specify which protocols, port numbers, and IP addresses are allowed to access instances. For instance, a common best practice is to only allow SSH traffic (port 22) from trusted IP addresses, ensuring that remote administrative access is restricted.
| Feature | Security Groups |
|---|---|
| Scope | Instance-level |
| State | Stateful |
| Direction | Controls both inbound and outbound traffic |
| Number of Rules | Flexible, with limits on inbound and outbound |
Control traffic to your AWS resources using security groups - Amazon VPC
Section 2: Differences Between Security Groups and NACLs
While both Security Groups and Network Access Control Lists serve to control traffic, they operate at different levels within the VPC architecture. Understanding the differences between these tools is essential for configuring secure environments.
| Feature | Security Groups | NACLs |
|---|---|---|
| Scope | Instance-level | Subnet-level |
| State | Stateful | Stateless |
| Default Action | Implicitly denies all inbound | Allows or denies based on rules |
| Rule Evaluation | Evaluated as a cumulative set of rules | Rules evaluated in a specific order (numbered) |
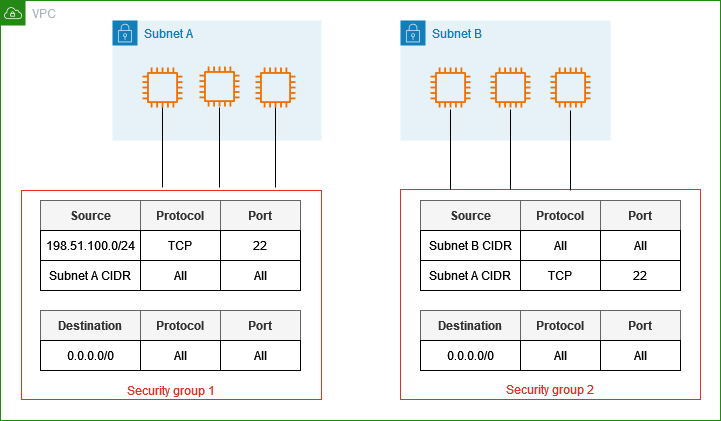
Stateful vs Stateless: Security Groups are stateful, meaning that any traffic allowed in will automatically be allowed out, without the need for explicit outbound rules. NACLs, on the other hand, are stateless, requiring both inbound and outbound rules for every direction of traffic.
Use Cases: Security Groups are ideal for managing traffic at a more granular instance level, whereas NACLs are often used to control subnet-level access, providing an additional layer of defense.
Best Practices for Using Security Groups
Implementing Security Group Rules
To secure AWS resources, DevOps teams must adhere to some best practices when defining Security Group rules.
Principle of Least Privilege: Only permit access that is absolutely necessary. For example, instead of leaving an HTTP port (80) open to all IP addresses, restrict it to trusted addresses. This limits exposure and potential attack surfaces.
Regular Audits and Cleanup: Over time, projects evolve, and so do their network security requirements. Regularly auditing Security Groups helps remove redundant rules and ensures compliance with the Principle of Least Privilege.
| Best Practice | Description |
|---|---|
| Least Privilege | Ensure access is only granted where necessary |
| Network Segmentation | Use multiple security groups to segregate traffic logically |
| Audits | Regularly review and remove unnecessary rules |
Security Group Integration with DevOps
Security Groups should be integrated into the CI/CD pipeline to automate security in a DevOps environment.
Automation: Utilizing Infrastructure as Code (IaC) tools like Terraform or AWS CloudFormation to define and manage Security Groups provides consistent and reproducible configurations. These tools help automate the creation and updating of Security Groups, ensuring they are applied consistently across all instances.
Monitoring Changes: AWS offers services like AWS Config to monitor Security Group changes in real time. This is essential for maintaining security compliance, as it provides visibility into any unauthorized modifications.
Security Groups are critical to securing AWS instances, providing a first line of defense against unauthorized access. Understanding the differences between Security Groups and Network Access Control Lists (NACLs), and implementing best practices, is essential for developing a robust security strategy in any AWS environment. By following best practices such as the Principle of Least Privilege and integrating Security Groups into your DevOps pipelines, you can enhance the security posture of your cloud infrastructure effectively.
Leverage tools like AWS Config and Infrastructure as Code solutions to make the process streamlined and compliant with modern DevOps methodologies. Understanding these components not only helps in preventing unauthorized access but also builds a strong foundation for scaling cloud-based applications with a focus on security.