Effective Identity and Access Management (IAM) in AWS
Managing identities and access in AWS is fundamental to ensuring the security and efficiency of cloud resources. It is crucial to understand how AWS Identity and Access Management (IAM) provides centralized control over your cloud infrastructure, allowing you to enforce least privilege and secure every interaction. In this blog post, we will explore the foundational aspects of AWS IAM, delve into credential types, and examine additional services that enhance identity and access management. The focus will be on maintaining best practices, enhancing security, and automating processes wherever possible.
AWS IAM Users and Groups
AWS IAM serves as the backbone for creating and managing users, groups, and permissions across your AWS resources. This centralized mechanism allows you to effectively control who has access to what, ensuring security while providing necessary access to developers, administrators, and other roles.
| IAM Users and Groups |
|---|
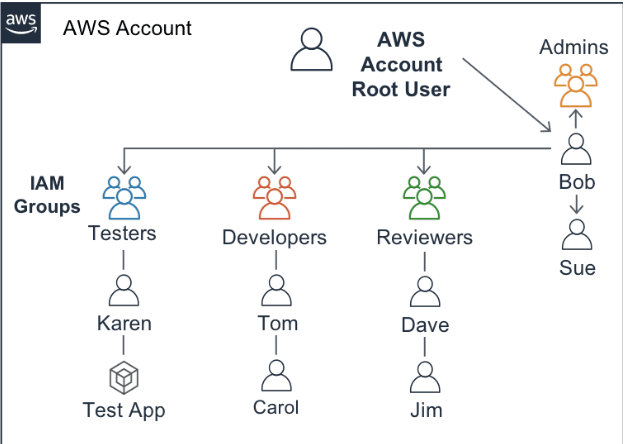 The image above shows how IAM groups may be used to organize users and specify permissions. |
Key Concepts of IAM Users and Groups
- Centralized Identity Management: IAM enables centralized management of user accounts and credentials. The first identity you create in AWS is known as the root account, which has unlimited access. From there, you create IAM users with minimal privileges to carry out specific tasks.
- Group Management: By grouping similar types of users (e.g., “Developers”), you can assign permissions collectively, simplifying management. It’s recommended to assign permissions to groups rather than individual users for easier auditing and modification.
Real-world Example: In a typical enterprise, you could create an IAM group called “Developers” with permissions to access only development resources such as EC2 instances in a development environment. Using role-based access simplifies managing permissions as the team grows or evolves.
Types of AWS Credentials
AWS provides multiple credential types to authenticate users and applications. These credentials ensure secure communication and interaction with your AWS environment.
| AWS Credential Types | Description |
|---|---|
| Username & Password | Used for AWS Management Console access. Enforce strong password policies for enhanced security. |
| Multi-Factor Authentication (MFA) | Adds an extra layer of security for AWS users. Always implement MFA for highly privileged users. |
| User Access Keys | Allows programmatic access using AWS CLI, SDKs, or API. They consist of an Access Key ID and a Secret Access Key. |
| Amazon EC2 Key Pairs | Used for SSH/RDP access to EC2 instances. AWS recommends using directory-based access for enhanced accountability. |
Credential Management and Best Practices
- Password Policy: Define a password policy that mandates the use of strong passwords, frequent rotation, and, where applicable, prohibits the reuse of old passwords.
- Multi-Factor Authentication (MFA): MFA should be a default requirement for any IAM user with console access. This includes deploying hardware or virtual MFA tokens for an extra security layer.
- Access Keys: Access keys should only be created when necessary. Use AWS Secrets Manager to manage, rotate, and secure access keys when programmatic access is required.
DevOps Insight: As a DevOps engineer, automate credential rotation using AWS SDK and configure alerts for any unauthorized access attempts. Regularly audit access keys and rotate them to mitigate risks.
AWS Credentials and Access Management
Additional AWS Services for Identity and Access Management
Beyond IAM, AWS offers several services that further enhance identity and access management, particularly for large organizations or those needing complex access patterns.
Use Case: AWS IAM Identity Center for Enterprise SSO
AWS IAM Identity Center allows for single sign-on (SSO) across AWS accounts and business applications, making it a powerful tool for enterprises managing multiple environments. By integrating with Microsoft Active Directory, organizations can streamline identity management and leverage existing credentials for AWS access.
- Implementation Tip: For companies with a large workforce, integrating IAM Identity Center with Active Directory provides a unified approach to managing access across AWS services, minimizing friction in adopting new tools.
AWS IAM Identity Center Overview
Identity and Access Management (IAM) in AWS is a critical aspect of securing your cloud resources and maintaining control over who has access to what. By leveraging IAM users, groups, and roles effectively, DevOps engineers can uphold the principles of least privilege and security best practices. AWS services like Secrets Manager, IAM Identity Center, and AWS Organizations offer further capabilities for centralizing access management and enhancing security.
When designing your IAM strategy, always focus on enforcing strong authentication, ensuring least privilege, and automating wherever possible to reduce human error. Embrace tools like AWS Organizations for policy-based management, and remember to integrate MFA and audit access keys regularly for maximum security.
For further information, consider reading AWS Security Best Practices to dive deeper into maintaining a secure AWS environment.



