AWS Global Infrastructure - Optimizing Resource Deployment Across Regions
When utilizing AWS services, understanding the infrastructure that underpins the security of your data is vital. AWS employs robust physical, environmental, and infrastructural security measures to protect data centers worldwide. This blog post aims to provide an in-depth examination of AWS data center security from the perspective of a DevOps engineer and programmer, ensuring you understand how security best practices are implemented at different layers: the Perimeter, Environmental, Infrastructure, and Data Layers.
This layered approach forms the basis for a secure computing environment, allowing organizations to confidently build scalable, reliable, and compliant cloud solutions without worrying about physical threats to their data. In this post, we’ll explore each of these layers, providing real-world applications, best practices, and implications for both cloud security and software development.
The Perimeter Layer: Physical Security Starts Here
Keeping Unwanted Threats Outside
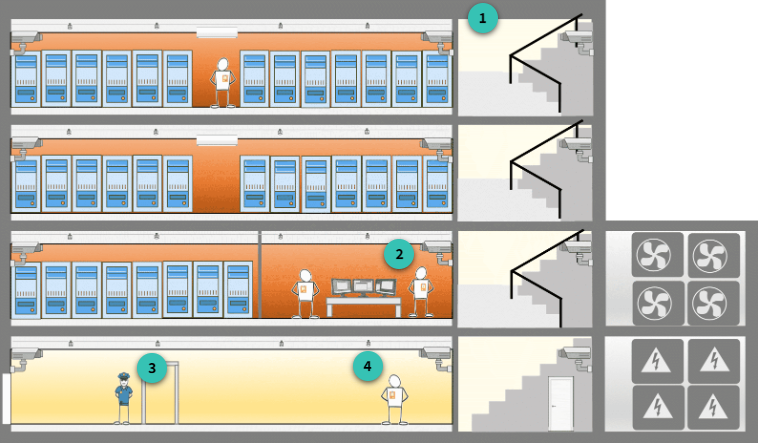
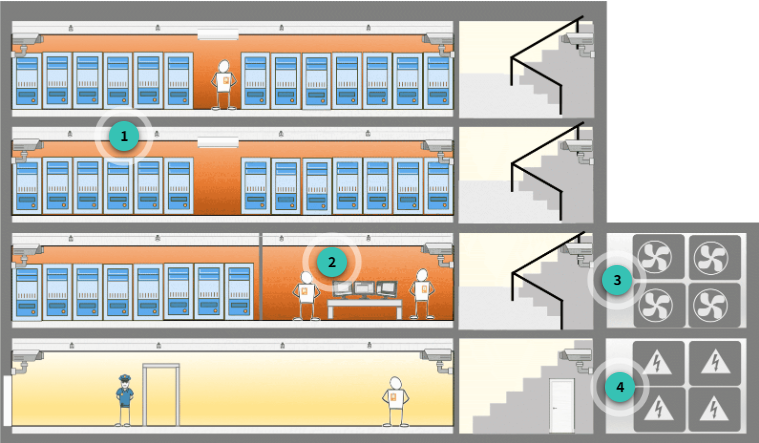
The perimeter layer is the first line of defense in AWS’s approach to securing their data centers. It includes physical barriers such as fences, professional security staff, and advanced monitoring systems.
Surveillance and Access Control: AWS data centers are housed in nondescript, undisclosed facilities—these locations are deliberately kept low-profile to deter potential threats. Video surveillance, intrusion detection systems, and access log monitoring are all deployed to ensure that unauthorized personnel cannot access the premises.
Principle of Least Privilege: The concept of the Principle of Least Privilege is implemented strictly. Only those AWS employees and contractors who have a legitimate business need are provided access to specific areas within the data center. Even when granted, these privileges are limited to the extent required to perform their job. For example, if a technician needs to enter a particular zone, access will be approved only for that area and nothing more.
This proactive approach to minimizing physical security risks directly impacts how secure the services hosted in these data centers are. As a DevOps engineer, it’s crucial to understand that the foundation of cloud security lies in safeguarding the physical locations that house your data.
AWS Physical Security Protocols
The Environmental Layer: Mitigating Natural Risks
Designing for the Unexpected
The environmental layer ensures that AWS data centers are resilient to natural disasters and environmental threats. This involves careful selection of data center locations to mitigate risks from flooding, extreme weather, and seismic activity.
Environmental Risk Assessment: AWS carefully selects the locations of its data centers by evaluating environmental risks. For instance, data centers are rarely, if ever, located in areas prone to frequent natural disasters, such as earthquake zones or regions with a high probability of hurricanes.
Climate Control and Business Continuity: Climate control systems are essential for keeping servers at the optimal temperature, thus reducing the risk of overheating and subsequent service outages. Moreover, AWS routinely conducts drills to test its Business Continuity Plan to prepare for unforeseen environmental scenarios. This includes simulations that help identify gaps in contingency planning.
For developers and DevOps professionals, this meticulous preparation translates into reduced downtime and higher availability, making AWS a reliable partner in any production environment. It also helps organizations meet high Service Level Agreements (SLAs), which are crucial for client trust.
AWS Environmental Control Measures
The Infrastructure Layer: Protecting the Backbone of AWS Services
Backup Power, Fire Prevention, and More
At the infrastructure layer, AWS ensures that the essential components of their data centers, such as HVAC systems, fire suppression, and backup power, are maintained to keep operations running smoothly.
Fire Detection and Prevention: AWS data centers are equipped with fire detection and suppression systems. Smoke detection sensors are strategically placed throughout the data center, from mechanical spaces to chiller rooms. In the event of a fire, automatic suppression systems activate to protect equipment and, by extension, the data residing on it.
Redundant Power Systems: To prevent power-related service interruptions, AWS uses fully redundant power systems. Each data center has Uninterruptible Power Supplies (UPS) that provide backup power to critical components, while diesel generators serve as additional backup to keep the data center operational in case of prolonged power outages.
The infrastructure layer exemplifies the value of redundancy and preparedness, which are also fundamental principles in software engineering and DevOps practices. Just as servers are backed up, so too are the power systems and life support mechanisms within AWS data centers. This mindset encourages DevOps professionals to apply similar principles when designing infrastructure for redundancy—using tools like Auto Scaling and Elastic Load Balancing to ensure availability.
AWS Infrastructure Layer Security
The Data Layer: Ensuring Data Integrity and Compliance
Protecting Customer Data
The data layer focuses on the security of the data itself. AWS ensures that customer data, from creation to deletion, is handled securely:
Data Destruction: When storage devices are no longer in use, AWS follows the NIST800-88 standard to ensure customer data is thoroughly and securely destroyed. This guarantees that data cannot be recovered once a device is decommissioned.
Data Auditing: AWS works with external auditors who review the data center security practices and verify adherence to compliance standards. This not only builds customer trust but also helps organizations maintain compliance with regulations like GDPR or HIPAA, which are often required depending on industry and location.
Monitoring and Alerts: AWS also employs advanced monitoring for all data-related activities. If an attempt to tamper with data is detected, the involved server can automatically disable itself to prevent a breach, ensuring your data remains safe from unauthorized actions.
For DevOps engineers, the take-home message is clear: data protection is an ongoing process. This responsibility involves both technical measures (e.g., encryption and access controls) and operational diligence, such as regular audits and adherence to best practices for data lifecycle management.
AWS’s Data Center Security represents one of the most robust and multifaceted approaches to securing cloud infrastructure, encompassing physical, environmental, infrastructural, and data-specific layers. Each layer provides unique protection mechanisms that collectively ensure the integrity, availability, and confidentiality of customer data. As DevOps engineers and programmers, understanding the security mechanisms in place helps to build confidence in the platform and informs decisions about architecting secure, resilient cloud applications.
By integrating AWS’s security principles into your own cloud environments, you can create solutions that leverage the best of what AWS has to offer—enhanced availability, stringent compliance, and unparalleled security. Whether deploying applications in production or storing sensitive customer information, AWS’s approach ensures that you have the tools and foundation necessary to protect against both physical and digital threats.
To learn more about AWS’s data center security and compliance measures, consider exploring AWS Compliance and the AWS Security Best Practices. These resources provide deeper insights into creating effective, compliant, and secure cloud environments.